Distributed ledger technology (DLT) is more than just blockchain. There are a wide variety of solutions that use different architectures to verify the accuracy of data.
Distributed ledger technology (DLT) is a popular method for securely replicating, sharing, and synchronizing data across a distributed computer network. It offers an alternative to centralized databases, which rely on a single server or small network to function. This creates a single point of failure, making centralized systems vulnerable to attack. Blockchain is by far the most well-known distributed ledger technology, yet several other types exist.
In this article, we’ll define exactly what are distributed ledgers and explain how they work to verify the accuracy of data. We’ll compare public ledgers and private ledgers. Finally, we’ll look at how four prominent types of DLTs work.
Key Takeaways
- Blockchain is just one type of distributed ledger technology. There are many others, including Directed Acyclic Graph (DAG), Holochain DLT, and Tempo (Radix).
- Distributed ledgers are a useful way to record data, distribute information to multiple parties, and protect against data tampering.
- Distributed ledgers can be public (open to everyone to view and verify data) or private (restricted to a select few participants).
Why Are Distributed Ledgers Useful?
No Middlemen
Distributed ledgers remove middlemen from data distribution and verification. Instead of having to rely on a single company or institution to maintain a central server, a collective group of operators accomplish this together. One benefit of this is lower fees (sometimes even zero fees) to send data across the network.
Transparency
Data on distributed ledgers, especially public blockchains, is transparent. This means it is easy for anyone to verify data in real-time at any time. It's also more difficult for companies to profit off of user data.
Tamper Resistance
Because data on a distributed ledger requires a majority of participants to agree upon (consensus), the network is much more tamper-resistant than traditional, centralized ledgers.
What Is A Distributed Ledger Technology?
A distributed ledger is a peer-to-peer network that doesn’t have a central administrator or central database. This design is intended to increase network security and remove corruption by replacing a single point of failure with a distributed network of devices that work together to verify the accuracy of data. Although distributed ledgers have major technical differences and serve different purposes, all of them generally require a few components to function.
Common Components of Distributed Ledgers
- Peer-To-Peer Network - Created when two or more computers establish a connection to communicate and share information without going through a central server. Peer-to-peer networks improve upon the security of client-server networks, which only store data on the server side.
- Nodes - Independent computers that record, share, and synchronize transactions in distributed ledgers. Nodes in a network are connected to each other and act as communication points. A higher number of nodes verifying data generally equals greater security in scenarios such as power outages or malicious attacks. Some distributed ledgers use masternodes, which perform the same functions as regular nodes, in addition to participating in governance, such as voting events, and execution of important protocol operations.
- Consensus Mechanisms - The set of rules that determine how DLT networks reach agreement on whether changes to the ledger are valid or invalid. Consensus protocols ensure that nodes on distributed ledgers have consistent, valid information. Proof of Work and Proof of Stake are two popular types of blockchain consensus protocols for public blockchains.
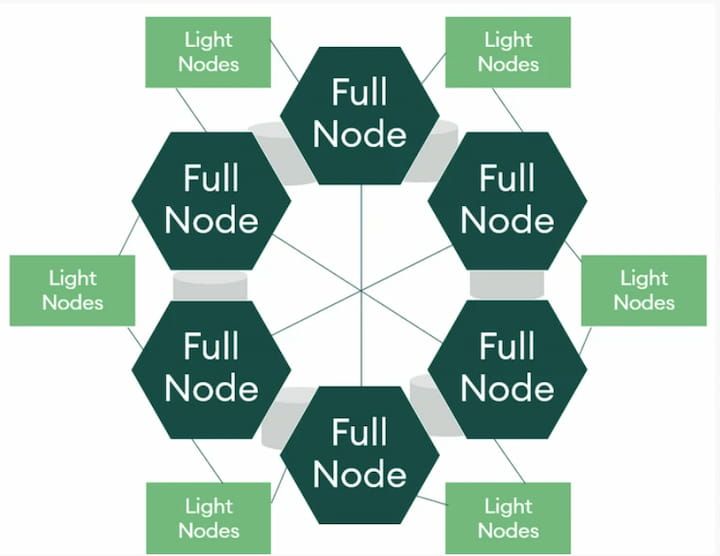
How Distributed Ledger Technology Works
Distributed ledger technology solutions can vary in their design, but all seek to achieve similar goals. Before looking at the technology side in more detail, let’s use an analogy to understand how distributed ledgers work and how they can be applied to improve existing systems.
The Town Analogy
Imagine that there is a small town of 10 people. Each person participates in the economy and has specific responsibilities.
Alice harvests crops. Bob catches fish. Others are responsible for building houses, cooking meals, and other crucial tasks for the town to flourish.
One day, Alice wants to trade crops for fish but realizes that the crops aren’t yet ready for harvest. She asks Bob to make the trade anyway. He agrees and says Alice can repay the favor after she has harvested her crops. Over time, though, the two may have too many favors to keep up with. The system only gets more chaotic when the other townspeople are factored in.
Alice, Bob, and the other villagers in the community agree to appoint a man named John to be the sole keeper of the town ledger. John is in charge of keeping track of all favors and loans, as well as repayments, making sure everyone is contributing to the local economy. John writes all favors down on a sheet of paper that only he can access. Although this system works for a little while, issues arise when John realizes how much power he has compared to the other villagers.
John is often bribed by people to add or erase favors from the ledger. John’s power goes unchecked until one day the townspeople finally get tired of this system. They decide to create a distributed ledger, meaning everyone in the town has access to the same piece of paper and pen. The ledger is placed in the town square for everyone to record both favors and repayments. Any disputes are settled through community votes. The favor system becomes transparent and far less corrupt than when John was the only one in charge of the ledger.
Analogy Conclusion
By this point, it should be clear that today’s distributed ledger technology is an attempt to solve an age-old problem of recordkeeping. The main difference is that the solutions being developed and used today are vastly more complex and powerful than a pen and paper ledger. Distributed ledger technology solutions are trying to be scalable enough to help the town, regardless if the population is 10 or 10 million.
Public Ledgers Vs. Private Ledgers
No matter which distributed ledger technology you want to use, there are two general system designs implemented: public ledgers and private ledgers. Let’s see how they compare.
Public (Permissionless) Ledgers
Public ledgers, oftentimes called permissionless ledgers, are usually open to everyone. They are decentralized, meaning no one person or company has control of the network. In the context of development, this often means any developer can create an application on top of the ledger without permission from anyone. For end users, permissionless means anyone can access the ledger for a variety of purposes, including storing and sending digital currencies, as well as using applications that are built on the ledger.
Private (Permissioned) Ledgers
Private ledgers, also called permissioned ledgers, are usually closed to a select group of users. They are centralized, meaning that one company or a small group of nodes are responsible for reaching consensus via the network’s consensus protocol. Developers are generally able to develop applications that run on top of the ledger, though these applications typically aren’t available to the public. In some cases, apps may be available but require users to get approval from an administrator. Most end users of private ledgers are currently large enterprises or governments. Private ledgers are typically used in scenarios that require restricted access (e.g. corporate blockchain supply chain management operations or military recordkeeping).
Examples of Distributed Ledger Technology (DLT)
In this section, we’ll cover the key differences between four distributed ledger technology solutions. One ledger may vary greatly from the another in terms of transactions per second and consensus mechanism, we won’t look at these categories. Instead, let’s compare data structures and transaction validation processes.
Distributed Ledger Technology And Blockchain: What’s The Difference?
The terms distributed ledger technology and blockchain are often mistakenly used interchangeably. The difference between the two is actually simple. Distributed ledger technology is a general term, with blockchain being one subcategory of DLT technology. Directed Acyclic Graph (DAG), Holochain DLT, and other subcategories of DLTs exist, but they aren’t as commonly known yet as blockchain.
We can think of the term “blockchain” sometimes being used in place of DLT as roughly the equivalent of saying Band-Aid to describe all adhesive bandages or Q-tips to describe cotton swabs. In all these cases, a specific term is used to refer to an entire class. For blockchain, the increased public recognition leads to more widespread usage, even in cases where the underlying technology being used is quite different from an actual blockchain.
Blockchain
Data on a blockchain ledger (otherwise known as a blockchain distributed ledger) has a distinct architecture. A blockchain is structured via blocks, which are ordered in a linear sequence according to when the validators on the network verify transactions. Validators are able to come to an agreement through consensus protocols to make important decisions, like whether to postpone legitimate transactions or cancel fraudulent transactions. As you'll learn in almost any guide about blockchain basics, validation for blockchains is sequential. For example, Block 1 must be created before Block 2, Block 2 before Block 3, and so on. This often creates a challenge since full nodes (distributed computers on the network) have traditionally needed to download the entire blockchain history. However, many projects are working on blockchain scalability solutions to ensure that blockchain application development can support large user bases.
The question of who validates transactions on a blockchain depends on the type of consensus mechanism being used. For example, Proof of Work consensus protocols rely upon miners who use specialized hardware mining equipment. Proof of Stake consensus protocols rely upon stakers who hold coins in their wallets. There are several different blockchain programming languages such as C++, Golang, and Java that play an important role in protocol development.
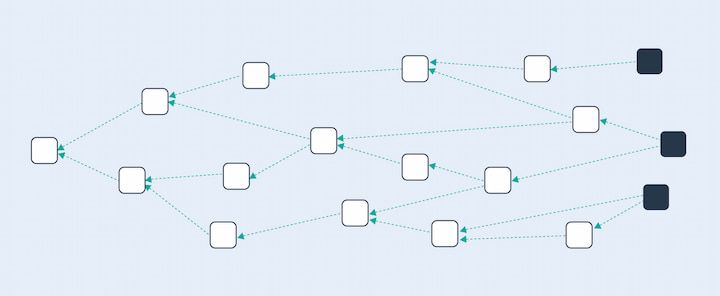
Directed Acyclic Graph (DAG)
Data on directed acyclic graphs (DAGs) does not require blocks or miners. Instead, all nodes are connected to each other. DAGs are described as graphs because they use a non-linear data structure consisting of nodes and edges. This means that transactions can be completed in a non-linear sequence.
In basic terms, Node A can be designed to communicate directly with Node C. Node B can also communicate with Node C. DAGs do have a defined structure, though. All data flow must be directed, meaning nodes communicate downstream. Edges are represented on DAGs as arrows that point in one direction on the graph. In other words, Node B or Node C can’t send information back to Node A. This design also means that DAGs are acyclic; therefore, they don’t allow for self-loops. Because data can’t flow upstream, DAGs work similar to blockchains in that they prevent issues such as transaction reversals on the distributed ledger.
Holochain DLT
Holochain DLT is different from other types of distributed ledgers due to the way in which nodes validate transactions. On blockchains, all nodes work to enforce global consensus across a single ledger. In contrast, Holochain DLT works by providing each node with its own signed hash chain. After data is signed to local chains, it is shared to a distributed hash table (DHT) where all nodes run the same validation rules. If someone breaks those rules, the DHT rejects their data and their chain forks away from the Holochain.
Whereas blockchains are typically limited in scalability and become less efficient with the introduction of more users, Holochain is actually designed to become more efficient when additional users come online. Since each user in Holochain DLT becomes its own host, efficiency increases with adoption.
Tempo (Radix)
Radix uses a data structure called Tempo, where nodes rely upon the passage of logical time to validate transactions. Radix implements logical clocks, a system based on Leslie Lamport’s logical clock theory. On Radix, logical clocks are essentially counters that count upwards in increments of 1 each time that a node sees a new, valid event on the ledger. The node checks its own database, increments its logical clock, stamps the event with a new timestamp and ID, and gossips it to the network. Periodic commitments via merkle trees are required to ensure that nodes don’t lie about the order of historical events on the ledger.
Komodo And Distributed Ledger Technology (DLT) Innovations
Now that we've looked at the distributed ledger technology definition and various examples, let's highlight how Komodo's solutions support blockchain use cases. There are many features that make Komodo unique from other blockchain platforms. Three examples are multi-chain design, independent chains, and customizable modular solutions.
While many blockchains only support one consensus protocol, Komodo enables projects to launch their own blockchains called Smart Chains and choose between Proof of Work, Proof of Stake, or any combination of the two.
Smart Chains run independently and never depend on the Komodo Platform, the Komodo blockchain, or the KMD coin. Smart Chains are customizable along 18 different parameters, giving projects full autonomy to determine premine coin supply, block time, block rewards, frequency and magnitude of reductions in block rewards, privacy settings, and much more.
All Smart Chains come with a library of powerful, built-in UTXO-based smart contracts to choose from. Tokens, Oracles, and quantum security are just a few Komodo Custom Contracts that Smart Chains can implement. Modules run at the consensus level, meaning that nodes verify with each use. This provides enhanced security over traditional smart contract platforms.
Want to become a blockchain developer? Read our Komodo Academy guides on topics such as blockchain developer skills and blockchain development courses.
📧Komodo Newsletter
If you'd like to learn more about blockchain technology and keep up with Komodo's progress, subscribe to our newsletter. Begin your blockchain journey with Komodo today.

