In the ever-evolving landscape of digital security, understanding the role and functionality of cryptographic hash functions is more crucial than ever. These functions are not just mere tools in cryptography; they are the backbone of digital security and integrity.
A hash function in cryptography is fundamental in various applications, from securing sensitive data to ensuring the authenticity of digital communications. This article delves into the world of cryptographic hash functions, offering insights into their definition, how they work, and their indispensable role in modern cryptography.
By exploring different examples, such as the 256-bit and SHA-512 cryptographic hash functions, and highlighting the differences between standard and cryptographic hash functions, we aim to shed light on these vital components of digital security. Whether you're a professional in the field or simply curious about the intricacies of cryptography, this article provides a comprehensive overview of cryptographic hash functions and their significance in our digital world.
Key Takeaways
- Foundation of Digital Security: Cryptographic hash functions are crucial for digital security, converting input data into fixed-size hash values. They ensure data integrity and authenticity, essential for password protection, digital signatures, and blockchain transactions.
- Mechanisms and Strengths: These functions operate through one-way, deterministic processes, making it impossible to reverse-engineer the original input. Their design allows for the secure handling of large data volumes, ensuring consistent and secure outputs in cryptographic applications.
- Varieties and Applications: Examples like the 256-bit and SHA-512 hash functions illustrate their diverse applications. The 256-bit offers a balance of speed and security, while the SHA-512 provides enhanced security for high-stakes data. The distinction between standard and cryptographic hash functions highlights essential features like collision resistance.
What Are Cryptographic Hash Functions?
Cryptographic hash functions are a cornerstone in the realm of digital security, serving as a fundamental component in various cryptographic operations. A hash function in cryptography operates by converting an input (or 'message') into a fixed-size string of bytes, typically a hash value.
The uniqueness of cryptographic hash functions lies in their ability to produce a distinct hash value for each unique input. This feature of a cryptographic hash function ensures that even the smallest change in the input will result in a drastically different hash value, an aspect known as the avalanche effect. In cryptography, the robustness of a hash function is gauged by its resistance to collisions, where different inputs should not yield the same hash value.
The Security and Reliability of Cryptographic Hash Functions
Whether it's for securing passwords, digital signatures, or blockchain transactions, the role of a hash function in cryptography cannot be overstated. The cryptographic hash function stands as a bulwark, ensuring that data remains tamper-proof and authentic, which is a pivotal feature of a cryptographic hash function in preserving digital security.
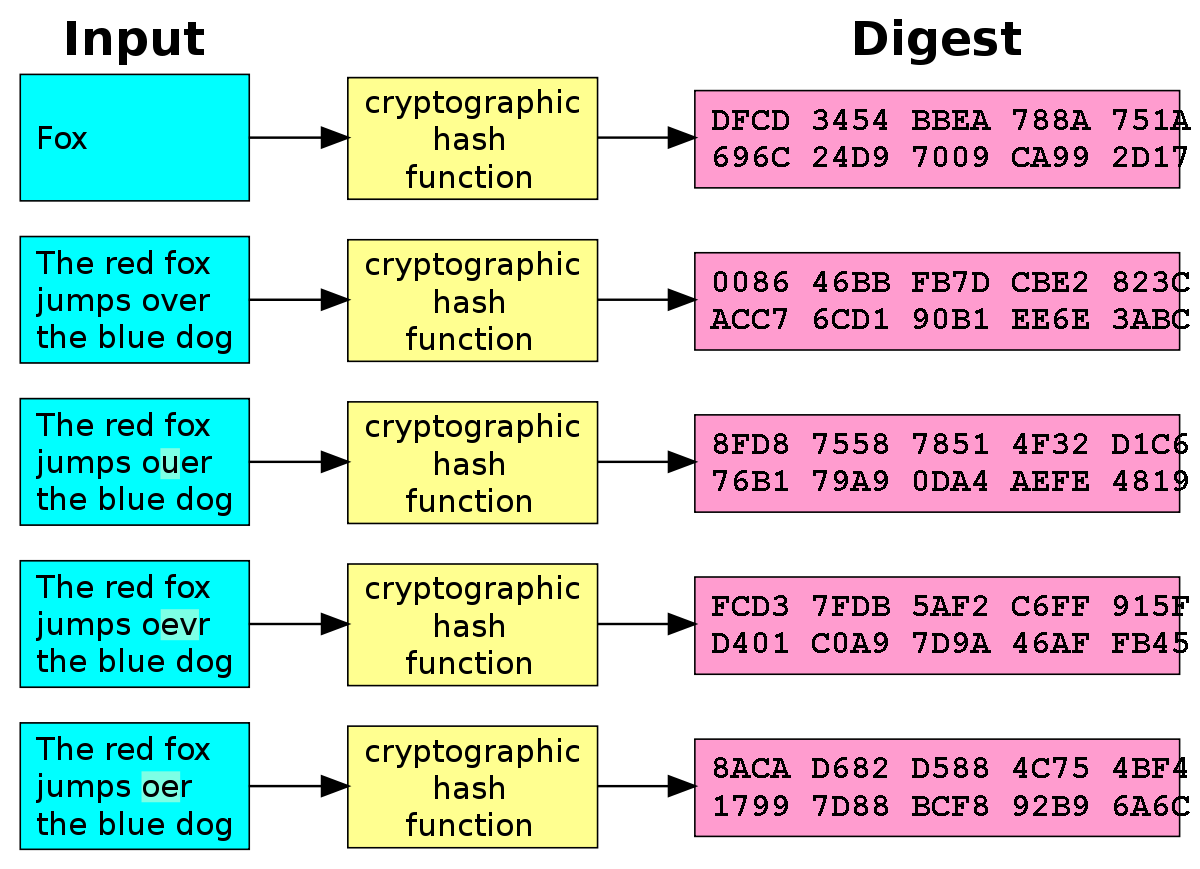
How Cryptographic Hash Functions Work
The inner workings of a cryptographic hash function are a marvel of cryptography, reflecting a sophisticated blend of mathematical and computational principles.
- At its core, a hash function in cryptography takes an arbitrary amount of data as input and processes it through a series of computational steps. These steps in the cryptographic hash function are designed to be one-way and deterministic.
- The one-way nature of a cryptographic hash function means that it is computationally infeasible to reverse the process, i.e., to deduce the original input from the hash value. This characteristic is crucial in cryptography, as it ensures the security of the data.
- Being deterministic implies that a given input will always result in the same hash value when processed through a particular hash function in cryptography. The output of a cryptographic hash function, the hash value, is typically a fixed-size string. This uniformity is vital in cryptography, as it allows for consistent handling of data irrespective of its original size.
- The strength of a cryptographic hash function in cryptography lies in its ability to handle large volumes of data swiftly and securely, making it an indispensable tool in digital security practices.
- The cryptographic hash function's role is pivotal in creating a secure and efficient environment for data management in various cryptographic applications.
Examples of Cryptographic Hash Functions
Cryptographic hash functions manifest in various forms, each tailored to specific applications in cryptography.
- One common example of a hash function in cryptography is its use in password verification. In this context, the cryptographic hash function transforms the user's password into a hash value, which is then stored instead of the plaintext password. This aspect of the cryptographic hash function enhances security, as the hash value cannot be easily reverted to the original password.
- Another significant application is in signature generation and verification. Here, a hash function in cryptography is used to create a unique hash of a message, which is then encrypted with a private key to form a digital signature. This process underscores the importance of the cryptographic hash function in ensuring data integrity and authentication.
- Furthermore, cryptographic hash functions play a vital role in verifying file and message integrity. By comparing the hash value of the received data with the expected hash value, a hash function in cryptography can ascertain whether the data has been altered or tampered with during transmission. This feature of a cryptographic hash function is fundamental in maintaining data integrity in various cryptographic scenarios. These examples highlight the versatility and indispensability of cryptographic hash functions in safeguarding digital information and maintaining trust in the digital world.
What Is the 256-Bit Cryptographic Hash Function?
The 256-bit cryptographic hash function represents a specific class of hash functions in cryptography, renowned for its high level of security and efficiency. This type of cryptographic hash function generates a fixed-size 256-bit (32-byte) hash value, an ideal size for robust security measures in various cryptographic applications. The strength of a 256-bit hash function in cryptography lies in its immense range of potential outputs (2^256 different possibilities), making it virtually impervious to collision attacks where two different inputs produce the same hash value.
The 256-bit cryptographic hash function is often utilized in securing blockchain transactions, where the integrity and authenticity of each transaction are paramount. This hash function in cryptography is designed to handle large amounts of data quickly and securely, offering a balance between speed and security. The cryptographic hash function with 256-bit output is also a standard choice for data encryption, digital signatures, and other cryptographic processes, thanks to its reliability and resilience against cryptographic attacks. In essence, the 256-bit cryptographic hash function stands as a pillar in the cryptographic community, offering an optimal blend of security and performance for safeguarding digital information.
What's the Difference Between a Hash Function and a Cryptographic Hash Function?
Understanding the distinction between a general hash function and a cryptographic hash function is crucial in the field of cryptography. While both types of hash functions transform input data into a fixed-size hash value, the cryptographic hash function is specifically engineered for security purposes in cryptography.
A standard hash function in data processing focuses primarily on speed and efficiency, ensuring that data can be quickly processed and retrieved. In contrast, a hash function in cryptography is designed with several key security features in mind.
Key Security Features of Cryptographic Hash Functions
The most important security feature is collision resistance, where it is computationally infeasible for two different inputs to produce the same hash value, and pre-image resistance, ensuring that it is virtually impossible to deduce the original input from its hash value.
Additionally, a cryptographic hash function exhibits the property of avalanche effect, where a slight change in input causes a significant change in the output hash value. This level of security is not typically a concern for standard hash functions.
Consequently, while a regular hash function is suited for general data management tasks like indexing, a cryptographic hash function is tailored for securing data, validating authenticity, and ensuring integrity in cryptographic applications. This distinction underlines the specialized role of cryptographic hash functions in maintaining the bedrock of digital security and trust.
What Is SHA-512 Cryptographic Hash Function?
The SHA-512 cryptographic hash function is a member of the Secure Hash Algorithm (SHA) family, specifically designed for enhanced security and robustness in cryptography. As a hash function in cryptography, SHA-512 generates a 512-bit (64-byte) hash value, making it one of the most secure hash functions available. The design of this cryptographic hash function is such that it can withstand sophisticated cryptographic attacks, including collision and pre-image attacks.
In cryptography, the SHA-512 hash function is particularly valued for its ability to process large volumes of data with a high degree of security. The cryptographic hash function's 512-bit length provides a significantly larger space for hash values compared to its 256-bit counterpart, offering an extra layer of security against potential cryptographic vulnerabilities. This makes the SHA-512 hash function an ideal choice for applications requiring top-tier security, such as high-level data encryption, secure banking transactions, and safeguarding sensitive government information.
The cryptographic hash function's robustness and reliability in handling data securely have cemented SHA-512's position as a preferred choice in the cryptography community for ensuring the highest levels of data integrity and security.
Conclusion
In conclusion, the role of a cryptographic hash function in the domain of cryptography is indispensable. The hash function in cryptography serves as a fundamental tool for securing digital data, ensuring integrity, and establishing trust in electronic environments. Whether it's in the form of a 256-bit or a 512-bit hash function, the cryptographic hash function stands as a testament to the advancements in digital security.
With the increasing reliance on digital platforms for communication, transactions, and data storage, the significance of a cryptographic hash function in maintaining a secure and trustworthy digital space is more pronounced than ever. As technology evolves, so will the capabilities and applications of hash functions in cryptography, continuing to safeguard the digital frontier against emerging threats and vulnerabilities.
FAQ
Why is Collision Resistance Important in Cryptographic Hash Functions?
Collision resistance ensures that it is computationally infeasible for two different inputs to produce the same hash value. This property is crucial for preventing malicious activities like forging digital signatures or tampering with data, as it ensures the uniqueness and integrity of the hashed data.
How Does the Avalanche Effect Enhance the Security of Cryptographic Hash Functions?
The avalanche effect ensures that a slight change in the input results in a significantly different hash value. This property enhances security by making it difficult for attackers to predict or control the hash output, thereby protecting the data from tampering and ensuring the integrity of the information.
What Are Some Common Uses of Cryptographic Hash Functions?
Cryptographic hash functions are widely used in various security applications, including digital signatures, message authentication codes (MACs), password hashing, and blockchain technology. They play a crucial role in ensuring data integrity, authenticity, and security across different cryptographic protocols and systems.
📧Komodo Newsletter
If you'd like to learn more about blockchain technology and keep up with Komodo's progress, subscribe to our newsletter. Begin your blockchain journey with Komodo today.

