SHA-256, or Secure Hash Algorithm 256, is a hashing algorithm used to convert text of any length into a fixed-size string of 256 bits (32 bytes).
In this article, we explore exactly how does SHA-256 work and why it was implemented on the Bitcoin network. We'll also look at its current effectiveness compared to other Proof of Work consensus algorithms.
Key Takeaways
- SHA-256's Role in Bitcoin: SHA-256 is a crucial cryptographic hash function used in Bitcoin's Proof of Work (PoW) consensus mechanism. It secures transactions by allowing miners to solve complex mathematical problems, ensuring the integrity of the network.
- Evolution and Security of SHA-256: Developed by the NSA in 2001, SHA-256 is part of the SHA-2 family of algorithms. It has been widely adopted beyond Bitcoin, securing over $1.2 trillion in digital currencies as of August 2024. Despite discussions of alternatives, SHA-256 remains robust due to its strong security properties.
- Mining Hardware Dominance: The advent of ASICs (Application-Specific Integrated Circuits) has significantly increased the efficiency of mining on SHA-256 networks like Bitcoin, but this has also led to centralization concerns, as only those with significant resources can compete effectively.
- Challenges with 51% Attacks: SHA-256 networks like Bitcoin, Bitcoin Cash, and Bitcoin SV have faced potential threats from 51% attacks, though these networks have managed to maintain security due to the high costs and resources required to execute such attacks.
- Emerging Alternatives: SHA-256 is no longer the only secure hashing algorithm available. SHA-3 and other hashing algorithms are considered faster and more secure, leading to the development of new blockchain projects that seek to address the limitations of SHA-256, such as lack of ASIC resistance.
What Is SHA-256?
- Originally published in 2001, SHA-256 was developed by the US Government’s National Security Agency (NSA).
- What is SHA-256 used for? This algorithm is commonly used in SSL certificates for websites and in the DKIM message signing standard for email clients. SHA-256 is a popular hashing algorithm used in Bitcoin encryption, first introduced when the network launched in 2009.
- Since 2009, SHA-256 has been adopted by a number of different blockchain projects, including several coins created from forks of the original Bitcoin source code.
- Among the top three SHA-256 blockchain projects by market capitalization — Bitcoin (BTC), Bitcoin Cash (BCH), and Bitcoin Satoshi’s Vision (BSV) —the SHA-256 mining algorithm secures over $1.2 trillion in digital currencies as of August 2024.
Why Is SHA-256 Important?
- How does SHA-256 work? The SHA-256 algorithm, like other hash functions, takes any input and produces an output (often called a hash) of fixed length.
- It doesn't matter if the input is a single word, a full sentence, a page from a book, or an entire book, the output of a hashing algorithm like SHA256 will always be the same length.
- Specifically, it will be 256 bits, which is 32 bytes, which is displayed as 64 alphanumeric characters. All outputs appear completely random and offer no information about the input that created it.
- Other important characteristics of SHA-256 include the fact that it is deterministic (it will always produce the same output when given the same input) and the fact that it is a one-way function. There is no way to reverse engineer an input from knowledge of the output.
- SHA-256 is computationally efficient and an ordinary computer can perform the operation dozens or even hundreds of times per second.
Learn more about hashing algorithms in this guide.
The SHA-256 algorithm is important because it's an integral part of mining on the Bitcoin network, as well as many smaller Proof of Work blockchain networks. Its role is particularly important, considering that Bitcoin (BTC) was the world's first blockchain and currently is the largest virtual currency by total market capitalization.

Enabling Proof of Work Mining
- SHA-256 was the first hashing algorithm used for verifying transactions on a blockchain network via a Proof of Work consensus mechanism.
- It’s important to note that Bitcoin wasn’t actually the first Proof of Work system. HashCash, a Proof of Work algorithm invented in 1997, is widely considered to be the first implementation.
- Satoshi Nakamoto cited HashCash as an influence for the Bitcoin network in the white paper: “To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back's Hashcash.”
- In basic terms, the SHA 256 hash supports a Proof of Work network in which computers race to solve a complicated math problem. After one computer finds a solution, it broadcasts that solution to the rest of the computers on the peer to peer network.
- PoW proves their work to the other machines that were trying to solve the same problem, as each computer on the network verifies the solution independently. If the solution is found to be accurate, the miner who found it is given a reward. Then, a new problem is presented and the competition begins again.
Learn more about cryptocurrency mining here.
Who Invented SHA-256?
SHA-256 isn’t the only algorithm in the Secure Hashing Algorithm (SHA) family.
It’s actually just one variation in a class of secure hash algorithms published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS).
Let’s examine how these algorithms have evolved over time.
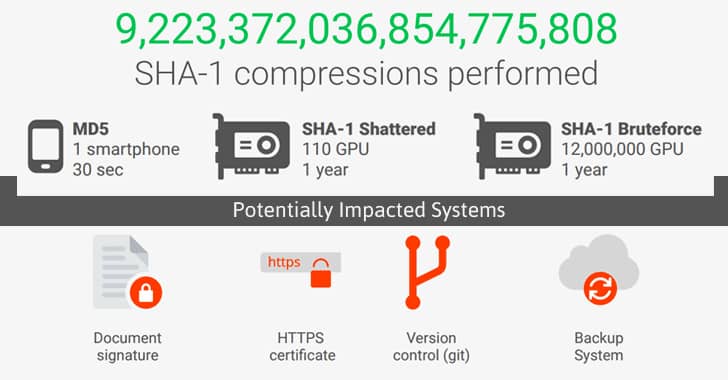
SHA-0 And SHA-1 Development
- SHA-0 is a 160-bit hash function first published in 1993 under the name “SHA.” Today, it is referred to as SHA-0 since more iterations were later developed. SHA-0 was withdrawn shortly after publication due to an undisclosed "significant flaw."
- Developed as a replacement for SHA-0, SHA-1 is a 160-bit hash function first published in 1995. It closely resembles the MD5 hash function, which was first published in 1992. SHA-1 was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm.
- Since 2005, SHA-1 is no longer recommended for cryptographic uses against well-funded opponents. SHA-1 was once widely used for SSL certificates, but this is no longer the case due to security weaknesses. For example, Microsoft stopped accepting SHA-1 certificates at the end of 2016.
- There is really no debate about whether to use sha1 vs sha256. The latter is clearly the more secure algorithm.
SHA-2 Development
- SHA-2 consists of two hash functions with different block sizes. SHA-256 was first published in 2001 and produces 32-byte outputs.
- SHA-512 was first published in 2004 and produces 64-byte outputs. SHA-224, SHA-384, SHA-512/224 and SHA-512/256 are truncated versions of these two standards.
- Just like SHA-1, all of the SHA-2 hash functions were developed by the NSA. The entire SHA-2 family is patented under US patent 6829355. While we do know who invented SHA-256, we don't know who invented Bitcoin.
- The patent for SHA-2 was released under a royalty-free license, making it available to people like Satoshi Nakamoto.
SHA-3
- The SHA-3 family, formerly known as Keccak, consists of four cryptographic hash functions: SHA3-224, SHA3-256, SHA3-384, and SHA3-512, and two extendable-output functions (XOFs), called SHAKE128 and SHAKE256.
- Extendable-output functions are different from hash functions, but it’s possible to use them in similar ways. The SHA-3 design was selected from a worldwide public competition of 64 hashing algorithm submissions and first published in 2015.
SHA-256 Algorithm in Blockchain
As you will see, the importance of SHA-256 algorithm in blockchain can't be understated. Bitcoin (BTC), Bitcoin Cash (BCH), and Bitcoin SV (BSV) are three well-known projects which use SHA-256 for data encryption on their respective networks. In this section, we’ll look at how each of these networks were started and the effectiveness of SHA-256 at maintaining network security.
Bitcoin (BTC)
- Bitcoin (BTC) has used the SHA-256 hashing algorithm since its launch in 2009. This has led to the emergence of new, increasingly powerful mining rigs over time. These new rigs are called Application-Specific Integrated Circuit (ASIC) miners.
- There have been major disagreements within the Bitcoin community about whether the network should take measures to increase ASIC resistance. Proponents say that ASIC resistance would help prevent the rise of mining farm monopolies and the possible centralization of BTC supply.
- There have also been discussions among developers about the idea of switching to a different hash function or transitioning to another blockchain consensus mechanism (e.g. Proof of Stake).
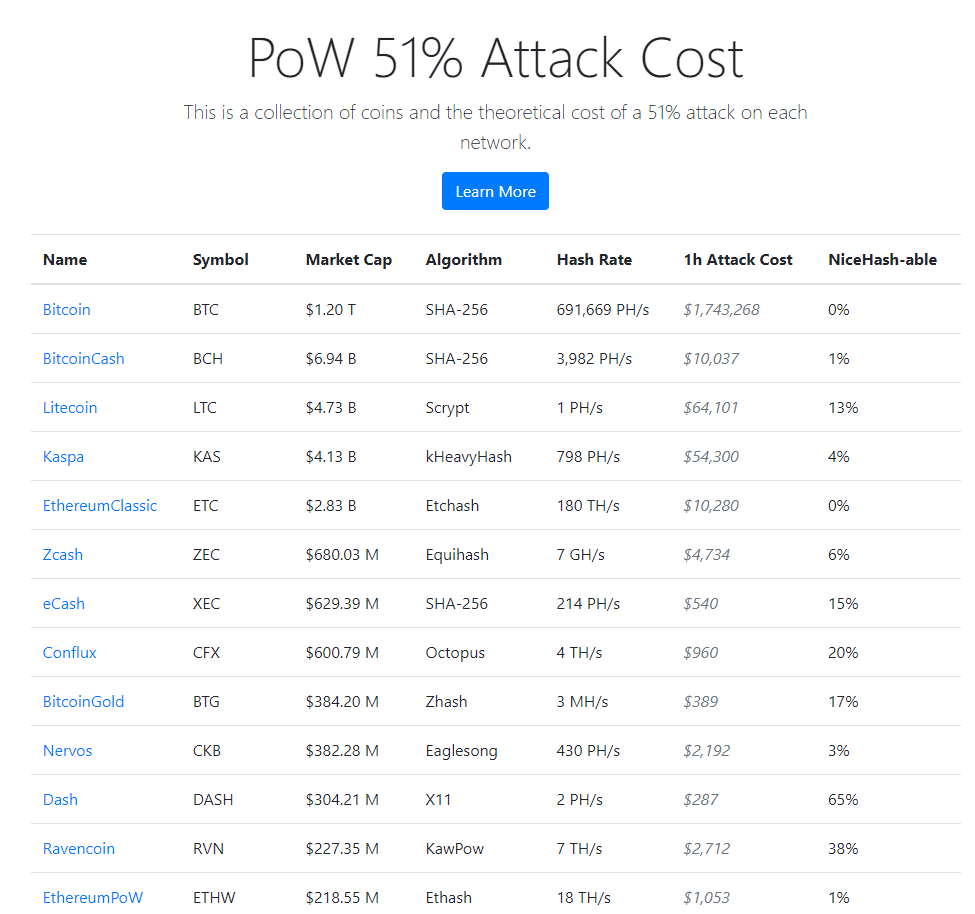
- Despite these concerns, no major changes have been made regarding the network’s use of the SHA-256 algorithm. This is likely because a majority of people prioritize network security over ASIC resistance. 51% attacks have never been an issue on the Bitcoin network.
- As of August 2024, the cost of electricity alone for a one-hour attack would cost more than $1.74 million. This figure does not include the amount of money that would be necessary to buy all of the hardware to launch such an attack. In reality, the cost of an hourly attack would be much, much higher.
- SHA-256 is also used along with another cryptographic hash function called RIPEMD-160 as part of “double hashing,” which is a step in the process of creating a Bitcoin address from a public key.
- So, why does the Bitcoin network use SHA-256? Satoshi Nakamoto answered this question in a comment in June 2010:
“SHA-256 is very strong. It's not like the incremental step from MD5 to SHA1. It can last several decades unless there's some massive breakthrough attack.If SHA-256 became completely broken, I think we could come to some agreement about what the honest block chain was before the trouble started, lock that in and continue from there with a new hash function.”
Bitcoin Cash (BCH)
- Bitcoin Cash (BCH) was created after a contentious hard fork of the Bitcoin network in July 2017. Some members of the Bitcoin community, including Roger Ver, believed that BIP 91 should have increased the network’s block size limit and disagreed with the implementation of SegWit.
- Bitcoin Cash implemented an 8 MB block size limit and later quadrupled the limit to 24 MB in May 2018. This project currently utilizes SHA-256. Some people think that continuing to use SHA-256 is a conscious decision to allow miners to easily switch their rigs back and forth between BTC mining and BCH mining, depending on which one is most profitable at any given time.
- Although Bitcoin Cash is a strong network, it has faced a few security challenges. In May 2019, an attacker exploited a bug that caused the network to split and prompted miners to mine empty blocks for a short time. Two bitcoin cash (BCH) mining pools— BTC.com and BTC.top— worked together for the common good of the network. Rather than using a 51% attack for nefarious means, they used this technique to reverse the attacker’s transactions.
- In October 2019, a report was published suggesting that the BCH network was at risk of a possible 51% attack because an unknown miner controlled 50% of the hashrate for 24 hours. In January 2020, BTC.top controlled 50.2% of the network’s hashrate, once again demonstrating the vulnerabilities of the network.
- As of August 2024, the current electricity cost of a one-hour attack is around $10,037, which is higher than many other cryptocurrency networks with similar market caps. As above, this figure only takes the cost of electricity into consideration, and not the cost of hardware, so this estimate is actually far lower than the real costs of launching an attack on the BCH blockchain.
Bitcoin SV (BSV)
- Bitcoin SV (BSV) launched in November 2018 as a contentious hard fork of the Bitcoin Cash network. Bitcoin SV proponents disagreed with proposed technical upgrades of the Bitcoin Cash network and decided to create the BSV network with a block size limit of 128 MB. Unlike the Bitcoin Cash split from the original Bitcoin network, the Bitcoin SV split from the Bitcoin Cash network wasn’t clear-cut.
- At the time of the hard fork, BSV and BCH started a “hash war” that lasted around 10 days. The goal of the BSV proponents was to perform a 51% attack that discouraged BCH mining and forced a major shift to BSV mining. This plan ultimately failed, and the hash war ended in a permanent split of the network into two distinct blockchains. This situation was made possible due to the fact that both projects implement SHA-256.
- As one analysis of Bitcoin vs. Bitcoin SV shows, miners on neither side of the hash war were unable to reach profitability. Both chains now run independently and still claim to be carrying out the original vision for Satoshi Nakamoto’s network.
- On the Bitcoin SV network, there were concerns expressed about a potential 51% attack in 2019 since one mining pool controlled a majority of the hashrate.
- In 2021, attackers successfully executed three separate 51% attacks against the Bitcoin SV network.
Limitations of SHA-256
When the Bitcoin network launched in 2009, SHA-256 was likely the most secure hash algorithm available. Since then, its limitations have become apparent. Here are a few notable examples.
ASIC Dominance
- It’s important to note that the SHA-256 hashing algorithm was never intended to be resistant against powerful machines. The debate over ASIC resistance on blockchain networks emerged well after the introduction of Bitcoin.
- According to one report, the evolution of Bitcoin mining hardware can be split into six generations. When the network launched in 2009, only CPUs were supported. This created a fair system for all miners on the network. This dynamic changed when later generations of mining equipment became publicly available.
- Each new generation of mining rigs was capable of producing more hash power than the previous one. The network was impacted by the emergence of GPUs (2010), FPGAs (2011), and ASICs (2012/2013). This made more affordable options like CPUs and GPUs less viable for cryptocurrency mining over time.
- ASICs clearly dominate the network today and are continuously becoming more powerful. This is clearly evident when examining a graph of the Bitcoin network’s all-time hash rate.
Current Mining Profitability
- Today, profitable mining of SHA-256 cryptocurrencies requires a powerful ASIC mining rig. Not all ASICs are capable of producing the same results, though. Let’s compare the Bitmain Antminer S19 Pro (projected release in 2020) with the Bitmain Antminer T15 (released in 2018). The S19 Pro will theoretically produce a significantly higher hashrate, thus reaching higher profits in the same timespan. However, miners also have to factor in that the S19 Pro retail price is almost 3x that of the T15 unit.
- Assuming that future machines will be even more powerful than the S19, it’s easy to see how ASIC mining tends to be ultra-competitive and requires a large capital investment. This form of cryptocurrency mining tends to favor a few well-funded individuals or corporations over the majority of ordinary miners.
Emergence of SHA-3 And Other Hashing Algorithms
- As we highlighted earlier, the SHA-2 family of algorithms is not the latest line of secure hash algorithms. SHA-3, formerly known as Keccak, is considered faster and more secure than SHA-256. SHA-3 is used by Nexus (NXS), SmartCash (SMART), and a few other blockchains.
- Like SHA-256, SHA-3 is ASIC friendly, making it difficult to mine SHA-3 cryptocurrencies with CPUs and GPUs.
- Many blockchain projects have cited the lack of ASIC resistance among all secure hash algorithms, specifically Bitcoin’s implementation of SHA-256, as a major reason for the development of other hashing algorithms such as Scrypt Mining Algorithm , Equihash, CryptoNight, and Lyra2REv2.
Custom Consensus Mechanisms With Komodo
The implementation of the SHA-256 hashing algorithm on Bitcoin's network paved the way for future innovations in blockchain consensus and the emergence of numerous blockchain use cases.
Komodo offers consensus solutions for any blockchain project. Using Komodo’s multi-chain network, you can launch an independent Smart Chain and fully customize the network’s parameters. Choices for consensus mechanisms include Proof of Work, Proof of Stake, or a hybrid combination of the two. If you choose PoW, you can select one of five different variations of the Equihash algorithm or the VerusHash algorithm. The PoS implementation can be used in combination with PoW consensus rules.
Komodo's Blockchain Security Service
For extra security against 51% attacks, Komodo’s delayed Proof of Work (dPoW) can be added as a secondary consensus mechanism on any UXTO-based blockchain, regardless of the consensus mechanism or hashing algorithm.
Komodo’s blockchain security service prevents potential attackers from re-organizing notarized blocks, effectively eliminating the threat of double spending. The dPoW mechanism uses the power of the Bitcoin network’s enormous hash rate to secure your blockchain, while also providing you with the ability to create a fair network for all miners and/or stakers.
📧Komodo Newsletter
If you'd like to learn more about blockchain technology and keep up with Komodo's progress, subscribe to our newsletter. Begin your blockchain journey with Komodo today.
FAQ
What are the main uses of SHA-256?
SHA-256 is commonly used in digital signatures, SSL/TLS certificates, cryptocurrency transactions (like Bitcoin), and integrity checks for data files and software.
Why is SHA-256 considered secure?
SHA-256 is designed to be resistant to collision attacks, where two different inputs produce the same hash output. Its complexity and large hash size make it computationally infeasible to reverse-engineer or find collisions.
How does SHA-256 differ from other hash algorithms like MD5 or SHA-1?
SHA-256 offers higher security compared to older algorithms like MD5 and SHA-1. It produces a longer hash value (256 bits vs. 128 or 160 bits) and is less vulnerable to cryptographic attacks, making it more suitable for modern security needs.

