SHA-512, or Secure Hash Algorithm 512, is a hashing algorithm used to convert text of any length into a fixed-size string. Each output produces a SHA-512 length of 512 bits (64 bytes).
This algorithm is commonly used for email addresses hashing, password hashing, and digital record verification. SHA-512 is also used in blockchain technology, with the most notable example being the BitShares network.
In this article, we explore the origins of SHA-512 and discuss how the algorithm has been used by BitShares as well other prominent blockchain projects. We’ll also look at a few examples of non-blockchain applications and examine how SHA-512 compares to the SHA-256 algorithm.
What is the SHA-512 Algorithm?
SHA-512 is just one of several algorithms in the Secure Hashing Algorithm (SHA) family. In 2001, SHA-512 was published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS).
Key Features of the SHA-512 Hash Function
- Robustness and Resistance to various cryptographic attacks — SHA-512 produces a fixed-size 512-bit hash value, providing a vast number of possible output combinations, which enhances its resistance to collision attacks.
- Logical and bitwise operations — Solutions such as modular addition and bitwise rotation ensure the unpredictability and irreversibility of the hash function. The algorithm is designed to handle input messages of up to 2^128 - 1 bits in length, making it suitable for a wide range of data sizes.
- Iterative Structure: SHA-512 employs an iterative process with multiple rounds of processing, each involving a set of specific mathematical functions. This iterative structure enhances the diffusion and avalanche effects, making it computationally infeasible to predict the hash output from small changes in the input.
- Versatility: While SHA-512 is commonly used for cryptographic purposes, it also finds applications in other fields, such as checksum verification and data integrity checks. Its versatility makes it a valuable tool for a wide range of information security and data management scenarios.
- Resistance to Birthday Attacks: The 512-bit output length significantly increases resistance to birthday attacks, a type of cryptographic attack that exploits the probability of two different inputs producing the same hash value. The large output space reduces the likelihood of such collisions, bolstering the security of the hash function.
Exploring the SHA-512 Hashing Process
From input formatting to hash buffer initialization, message processing, and generating the final output, each phase plays a pivotal role in shaping SHA-512's capability to provide reliable data integrity and cryptographic strength.
Input Formatting in SHA-512
In the SHA-512 hash function, the input formatting phase involves preparing the message for processing. The algorithm accepts messages of varying lengths and employs a padding scheme to standardize input sizes. Specifically, the message is padded with a series of bits to ensure it meets the necessary block size requirements for the algorithm. This padding includes the addition of a '1' bit followed by a series of '0' bits and a representation of the original message length. The input formatting phase ensures uniformity in message length, enabling SHA-512 to process messages of any size consistently.
Hash Buffer Initialization in SHA-512
Hash buffer initialization is a critical step in the SHA-512 algorithm that establishes the initial state of the hash function. The algorithm employs an 8-word hash buffer (A, B, C, D, E, F, G, H), initialized with specific constant values derived from the square roots of prime numbers. These initial values create a starting point for the iterative processing that follows. The hash buffer serves as a repository for intermediate hash values during the computation, evolving through multiple rounds of processing to ultimately produce the final hash output. Proper initialization is essential for the algorithm's security and the creation of a unique hash value.
Message Processing in SHA-512
The message processing phase in SHA-512 involves dividing the padded input message into blocks and iteratively processing each block. Each block undergoes a series of complex operations, including bitwise operations, logical functions, and modular addition, in multiple rounds. The input block is combined with the current state of the hash buffer, and the result becomes the new state for the next iteration. This iterative process ensures a high degree of diffusion and avalanche effects, making it computationally infeasible to reverse engineer the original input from the hash output.
H3: Generating the Output in SHA-512
The final phase in SHA-512 involves generating the hash output from the evolved state of the hash buffer. The 512-bit hash value is constructed by concatenating the values of the eight words in the hash buffer, creating a fixed-size representation of the processed input message. The resulting hash output exhibits properties such as collision resistance and unpredictability, forming the basis for its cryptographic strength. This final step in the SHA-512 algorithm produces a hash value that is unique to the input message, providing a secure and reliable means of verifying data integrity in various cryptographic applications.
The Role of SHA-512 in Digital Security and Cryptography
SHA-512 is also used in a variety of applications. It’s oftentimes used in conjunction with SHA-256 but sometimes used by itself.
H3: SHA-512 in Digital Certificates and Blockchain Technology
Compared to the SHA-256 algorithm, the adoption of the SHA 512 algorithm by blockchain projects has been very minimal. Most blockchain networks that chose not to implement SHA-256 opted for other hashing algorithms such as Scrypt, Lyra2REv2, Equihash, and CryptoNight.
- BitShares (BTS) — Although there isn’t any information available on the first blockchain project to implement SHA-512, we do know that BitShares (formerly ProtoShares) was one of the earliest to do so. According to the BitShares website, the network introduced the Momentum Proof of Work (PoW) algorithm in October 2013. Momentum is a proprietary graph-based algorithm that uses 512-bit SHA-1 (also known as Cuckoo Cycle). As one critique stated, there were at least two clear issues with the BitShares implementation of Momentum. First, the SHA-512 hash fails to take advantage of SHA-256 acceleration instructions. Second, this implementation was found to be needlessly slow. Both of these challenges meant ASIC miners would be able to succeed over CPUs and GPUs, leading to network centralization issues. The network’s genesis block was mined using Momentum PoW in November 2013. However, shortly afterward, BitShares founder Daniel Larimer determined that cryptocurrency mining was flawed. In July 2014, BitShares moved away from Proof of Work and became the first blockchain project to implement the Delegated Proof of Stake (DPoS) consensus mechanism.
- LBRY Credits (LBC) — LBRY is a protocol that allows anyone to build apps that interact with digital content (e.g. videos, audio files, documents, or any other type of file) on the LBRY network. Its native cryptocurrency is LBRY Credits (LBC), which can be used to access paid content on the network. LBRY has its own unique hashing algorithm that uses a combination of the SHA-512, SHA-256, and RIPEMD hash functions. The blockchain network has a targeted block time of 2.5 minutes, and the maximum size of each block is currently around 2 MB (around 1800 transactions). From Block 55001 onward, the network’s block reward decreases logarithmically over the course of a 20-year period. Cryptocurrency mining on LBRY is currently dominated by GPUs and FPGAs. The project team has stated that it no longer views CPU mining as economically viable.
SHA-512 in Internet Security
SHA-512 was used to authenticate archival video from the International Criminal Tribunal of the Rwandan genocide. Unix and Linux vendors use both SHA-256 and SHA-512 for secure password hashing. An email suppression list solution called OPTIZMO provides the storage and distribution of SHA-512 hashed email addresses for major clients such as Salesforce, LendingTree, Hotwire, and eharmony.
Comparing SHA-512 with Other Hashing Algorithms
Now that we understand how SHA-512 is used in real-world applications, let’s look at how it compares to SHA 256 vs 512 by assessing three critical factors: security, computational efficiency, and compatibility.
Security — SHA-256 And SHA-512 Compared
While there are a variety of potential attack vectors to evaluate, collision resistance is possibly the most important component of security for any hashing algorithm. The purpose of a hashing algorithm is to ensure that it’s virtually impossible to find two different inputs that produce the same output (known as a collision). If a collision is found, the accuracy of the original, unhashed message comes into question. Several collisions were found in SHA-0 and SHA-1, meaning those algorithms are not secure enough for real-world applications.
Since no technology is currently capable of breaking SHA-2 encryption and no collisions have been found, the security provided by SHA-256 and SHA-512 is practically identical. It’s theoretically possible that SHA-512 would have a slight security advantage given the rise of quantum computers. Nonetheless, it’s much more likely that all SHA-2 algorithms would need to be replaced with newer generations of quantum-resistant algorithms in order to effectively mitigate potential collision attacks.
Computational Efficiency — SHA-256 And SHA-512 Compared
SHA-256 produces smaller outputs than SHA-512. This means it generally requires less bandwidth to store and transmit data. Using SHA-256 generally requires less memory and also less processing power in some cases. As this test shows, SHA-256 is 31% faster than SHA-512 when hashing shorter inputs. Meanwhile, SHA-512 is only 2.9% faster when hashing longer inputs.
The Bitcoin network hashes a lot of smaller inputs (e.g. 33-byte public keys and 80-byte block headers), which likely explains why Satoshi Nakamoto chose SHA-256 over SHA-512. There's also the fact that SHA-512 is better on 64-bit processors, while SHA-256 is better on 32-bit processors. When the Bitcoin network launched in 2009, 32-bit processors were much more widely used than 64-bit processors. In addition, the requirement for higher rounds of blockchain consensus and larger block sizes of SHA-512 adds computational overhead that slows down the transaction validation process.
Compatibility — SHA-256 And SHA-512 Compared
Another factor for the limited adoption of SHA-512 is the potential for compatibility issues for both blockchain and non-blockchain applications. For example, with the depreciation of SHA-1 due to security vulnerabilities, SHA-256 was chosen as the default SSL/TLS certificates. Because SHA-512 isn’t widely implemented, a few compatibility issues exist that make it a less practical solution.
Had Bitcoin adopted SHA-512, it’s very likely that this hashing algorithm would play a more prominent role today in blockchain technology. Because SHA-256 was implemented on the Bitcoin protocol, other blockchain networks (e.g. Bitcoin Cash and Bitcoin SV) that have been created as a result of hard forks of Bitcoin also continue to use SHA-256. In turn, this has meant that powerful ASIC hardware mining rigs have been manufactured specifically for the SHA-256 algorithm.
For less established blockchain networks, it’s also much easier to win over miners by using a hashing algorithm that is compatible with their existing hardware. Even if a smaller network wanted to use SHA-512, the possibility of limited miner adoption may lead to major security issues like inexpensive 51% attacks due to low hash rates.
Additionally, within the Secure Hashing Algorithm family, SHA-3 (formerly known as Keccak) now provides a faster and more secure solution than both SHA-256 and SHA-512.
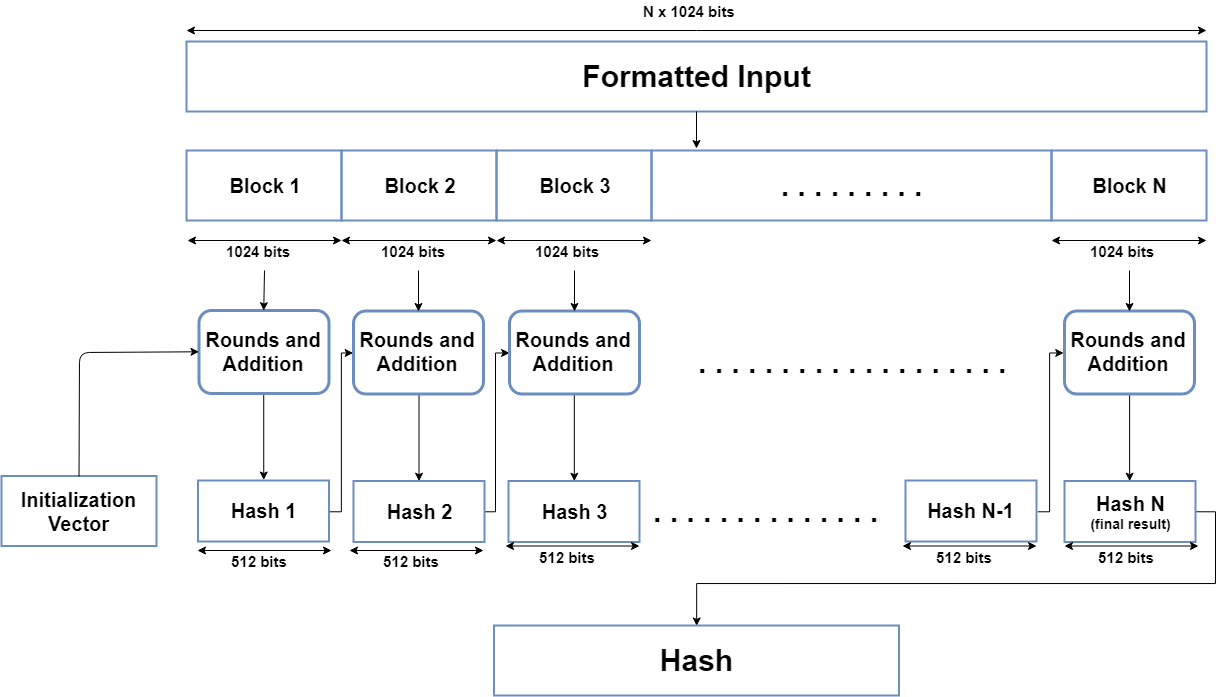
Visualizing the SHA-512 Algorithm
The following diagram shows how the SHA-512 algorithm works.
Conclusion: The Future Prospects of SHA-512 in Cryptography
SHA-512 hasn't been able to gain the same level of popularity as SHA-256 or even other types of newer hashing algorithms when it comes to real-world use in blockchain. That being said it does have a few non-blockchain applications that are noteworthy.
📧Komodo Newsletter
If you'd like to learn more about blockchain technology and keep up with Komodo's progress, subscribe to our newsletter. Begin your blockchain journey with Komodo today.

