P2PKH, or "Pay to Pubkey Hash" transactions in full form, are one specific type of payment in the Bitcoin Script.
How Does P2PKH Work?
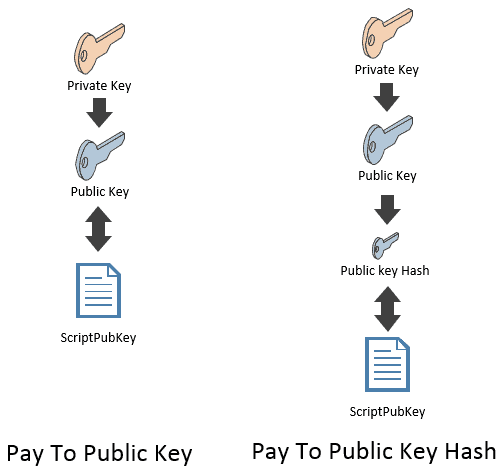
P2PKH transactions are similar to P2PK transactions, in that both payment types only require the recipient to prove ownership of their public key in order to receive the funds. The primary difference is that P2PK transactions are sent directly to the recipient’s public key, whereas P2PKH transactions are sent to the hash of the recipient's pub key. A hash is the output that results from putting a specific input through a hash function.
In this way, P2PKH is designed to provide more security and convenience for sending and receiving funds on a blockchain’s peer to peer network. This is largely due to two main advantages: public key hashing and error detection.
Public Key Hashing
P2PKH transactions use public key hashing to conceal public keys until the associated wallet spends funds, enhancing security by adding a layer between the private key and the public network. Pubkey hashes, being shorter alphanumeric sequences, are more user-friendly than full-length public keys.
Error Detection
In a P2PKH transaction, the receiver's Bitcoin address, a user-friendly form of a pubkey hash, is shared with the sender. This address, essential in P2PKH, includes a checksum for error detection. The process involves hashing the pubkey twice (SHA-256 algorithm and RIPEMD-160) to generate the pubkey hash used in P2PKH. Then, for P2PKH, this pubkey hash is converted to an address by adding version bytes, hashing again, and applying a checksum before Base58 encoding. P2PKH transactions are highly reliable, with a minuscule error acceptance rate, making P2PKH an effective and secure method in Bitcoin transactions.
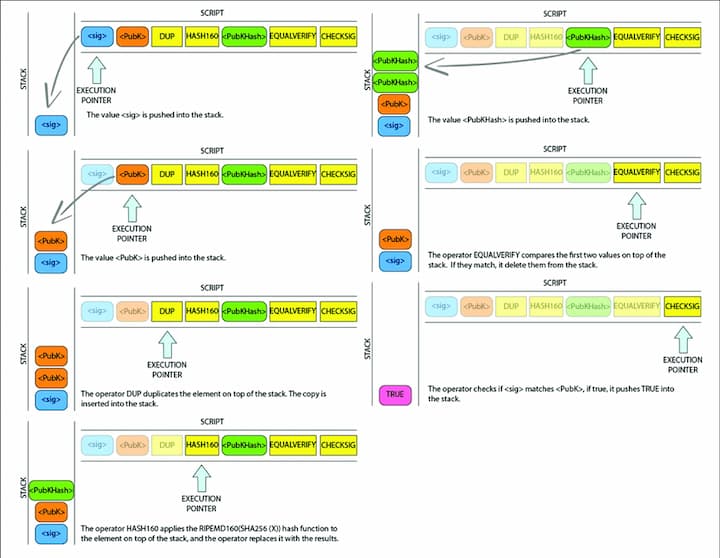
A Basic Example of a P2PKH Payment
In a P2PKH transaction, Alice first creates a key pair and converts her public key into a pubkey hash, then into an address. She shares this address with Bob, who sends BTC to it. Control of the funds is determined by matching a digital signature with Alice's public key and address. Bob and Alice only use pubkey hashes and addresses for interaction, enhancing security.
P2PKH, introduced alongside P2PK, remains crucial in Bitcoin transactions. It's more common than P2PK and less susceptible to quantum computing threats. P2PKH addresses, shorter than P2PK's pub keys, are user-friendly and include a checksum to reduce errors.
However, P2PKH's transaction setup is more complex, making it challenging for developers compared to simpler Bitcoin scripts like P2PK.
P2PKH and Its Role in Bitcoin Transactions Amidst SegWit Adoption
P2PKH, a widely used Bitcoin script, faces challenges with SegWit compatibility, unlike newer scripts like Pay to Script Hash and Bech32. As SegWit gains popularity, P2PKH, primarily for non-SegWit transactions, might see reduced use. Still, P2PKH is prevalent in the Bitcoin network.
Notably, P2PKH was used in the famous 2010 Bitcoin Pizza transaction. Even today, P2PKH remains crucial for Bitcoin, especially for its security, though other types are preferred for multi-sig transactions.
To spot P2PKH transactions, look for addresses starting with ‘1’ on blockchain explorers like BTC.com. These P2PKH addresses are common in recent transactions. Data from txstats.com shows a significant portion of Bitcoin, over 10.2 million BTC, is held in P2PKH wallets, with a high number of P2PKH unspent transaction outputs (UXTOs).
📧Komodo Newsletter
If you'd like to learn more about blockchain technology and keep up with Komodo's progress, subscribe to our newsletter. Begin your blockchain journey with Komodo today.

