In the rapidly evolving digital landscape, blockchain architecture stands out as a revolutionary technology, redefining how we think about data exchange and security.
At its core, the architecture of blockchain is ingeniously designed to offer a decentralized system, contrasting sharply with traditional centralized models. This structure of blockchain provides an unalterable digital ledger, facilitating transparent and secure transactions across a peer-to-peer network.
As we delve into the realms of blockchain architecture, it's crucial to understand its foundational elements – from the intricate structure of block in blockchain to the overarching network dynamics. This introductory exploration aims to demystify the complexities of blockchain architecture, setting the stage for a deeper understanding of its components and the transformative potential it holds.
Key Takeaways
Key Takeaways
- Decentralized and Secure: Blockchain architecture revolutionizes data exchange and security by offering a decentralized system, contrasting sharply with traditional centralized models. This structure ensures transparent and secure transactions across a peer-to-peer network.
- Historical Evolution: Originally conceptualized in 1991 to timestamp digital documents, blockchain technology gained mainstream attention with the creation of Bitcoin by Satoshi Nakamoto in 2008, marking a pivotal moment in its evolution.
- Core Characteristics: Blockchain's fundamental features include decentralization, robust security through advanced cryptographic techniques, and immutability of recorded data, which together enhance its reliability and transparency.
- Layered Architecture: Blockchain is composed of multiple layers, including the data layer (containing transactional information), the network layer (for peer-to-peer communication), the consensus layer (ensuring ledger integrity), and the application layer (enabling user-facing applications).
- Versatile Applications: Blockchain's structure supports various types of networks, such as public, private, hybrid, and consortium blockchains, each tailored for specific use cases ranging from open, decentralized systems to controlled, enterprise-focused environments.
Historical Context and Evolution of Blockchain Technology
The journey of blockchain architecture began far before its mainstream popularity. Initially conceptualized in 1991, the primary objective was to create a system for timestamping digital documents, ensuring they couldn't be backdated or tampered with. This foundational idea laid the groundwork for the structure of blockchain as we know it today.
However, it wasn't until 2008 that blockchain architecture truly took shape, thanks to Satoshi Nakamoto. Nakamoto's creation of Bitcoin, a blockchain structure based cryptocurrency, marked a pivotal moment in the evolution of this technology. This historical leap transformed the architecture of blockchain from a theoretical concept to a practical tool revolutionizing digital transactions. Understanding this evolution is crucial in grasping the intricate structure of block in blockchain, providing insights into its potential future advancements.
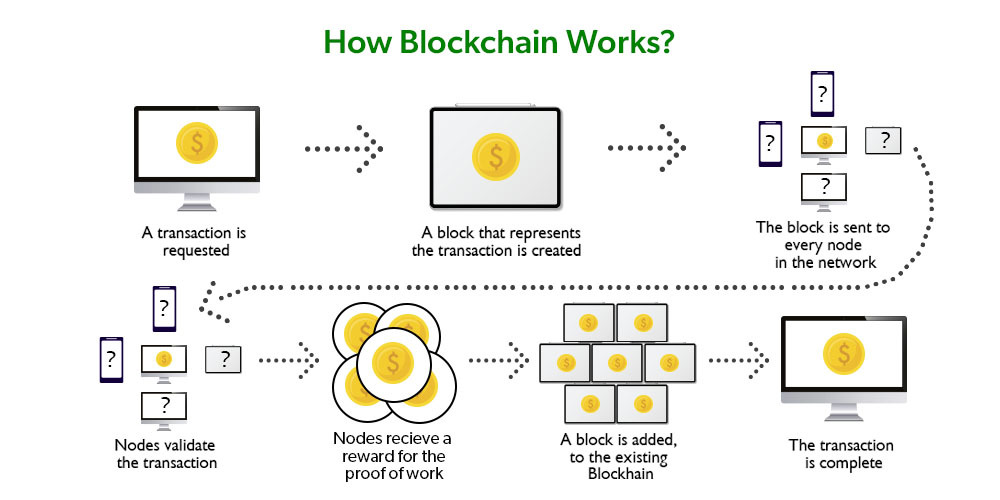
Deciphering the Structure of Blockchain
The structure of blockchain is akin to a digital backbone of a new type of internet, introducing an innovative way of sharing information. At the heart of this blockchain fundamentals lies its most defining characteristic - a secure and decentralized approach to data management. Essentially, each block in the blockchain structure serves as a record-keeping unit, securely interlinked with its predecessors and successors, forming an unbreakable chain.
The architecture of blockchain ensures that each block is tamper-proof, maintaining the integrity and trustworthiness of the entire chain. This structure of block in blockchain is not just a technical feat but also a paradigm shift in how data security and transparency are perceived and implemented. Understanding this structure is vital for appreciating the full scope of blockchain's potential in various sectors.
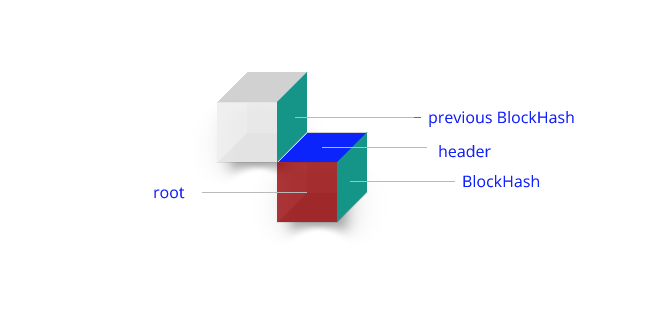
Core Characteristics of Blockchain Architecture
Delving deeper into the blockchain architecture, its core characteristics emerge as pillars of this revolutionary technology. The architecture of blockchain is fundamentally decentralized, eliminating the need for a central authority and thereby enhancing the system's robustness against failures and attacks. In this structure of blockchain, each participant, or node, plays a role in maintaining the network, leading to a more democratic and equitable digital ecosystem.
Another key aspect is the unyielding blockchain security inherent in the blockchain structure, provided by advanced cryptographic techniques. This blockchain security feature, combined with the meticulous structure of block in blockchain, ensures that once data is recorded, it becomes immutable – a permanent and unalterable part of the blockchain. These characteristics not only define the blockchain architecture but also open up a myriad of possibilities for its application in various sectors, from finance to supply chain management.
Understanding its Layers
The architecture of a blockchain is not a monolithic structure but rather a complex stack of multiple blockchain layers, each with its distinct role and function. At the base of this structure of blockchain is the data layer, where the actual blocks reside, containing transactional information securely linked using cryptographic hashes.
The network layer forms the next tier in the blockchain structure, responsible for the peer-to-peer communication essential for distributing information across the network.
Above this lies the consensus layer, a critical component of the architecture of blockchain, which ensures that all nodes agree on the state of the ledger, thus maintaining its integrity and trustworthiness.
The application layer sits at the top, where the structure of blockchain manifests into user-facing applications and services, making blockchain technology accessible and useful in real-world scenarios.
Understanding these layers is crucial for comprehending the full scope and versatility of blockchain architecture, paving the way for innovative applications that extend beyond cryptocurrencies.
Types and Variations in Blockchain Structure
Exploring the types of blockchain architecture reveals a diverse spectrum of applications and blockchain use cases.
Each type of blockchain structure serves specific needs and scenarios, highlighting the versatility and adaptability of blockchain architecture in various domains.
- Public Blockchains — Open to everyone, exemplifying the essence of decentralization seen in systems like Bitcoin and Ethereum.
- Private Blockchains — Offer restricted access, often employed by enterprises for confidential transactions and streamlined processes.
- Hybrid Blockchains — Blend elements of both public and private blockchains, offering a balance of transparency and privacy.
- Consortium Blockchains — Represent a collaborative model, where multiple organizations govern the network, ensuring a higher level of control and security.
The Building Blocks
At the heart of blockchain architecture lies the fundamental unit known as the block. Each block in the blockchain structure serves a critical role, acting as a ledger entry for transactions. Delving into the structure of block in blockchain, we find that it contains three key elements: transaction data, a unique hash that identifies the block and its contents, and the hash of the previous block, creating an unbreakable link in the chain.
This design is a cornerstone of the architecture of blockchain, ensuring that once a block is added to the chain, altering it retrospectively becomes nearly impossible. This immutability is a defining feature of the structure of blockchain, providing a level of security and trust that is unparalleled in traditional database systems. Understanding this block structure is essential to appreciate the full security and transparency that blockchain architecture offers.
Nodes and Networks
In the blockchain structure, nodes are the fundamental components that uphold the network's integrity and functionality. A node in the architecture of blockchain is typically a computer connected to the blockchain network, which actively maintains a copy of the entire ledger. This decentralized nature of nodes is what gives the blockchain architecture its strength and resilience. In a public blockchain structure, anyone can participate as a node, contributing to the network's robustness and security.
On the other hand, in a private blockchain architecture, node participation is restricted, offering a more controlled environment. These nodes play a crucial role in the validation and relay of transactions, forming a peer-to-peer network that is central to the blockchain structure. This setup ensures that the blockchain architecture remains transparent yet secure, as every node in the network works towards achieving consensus, validating transactions, and maintaining an identical copy of the ledger.
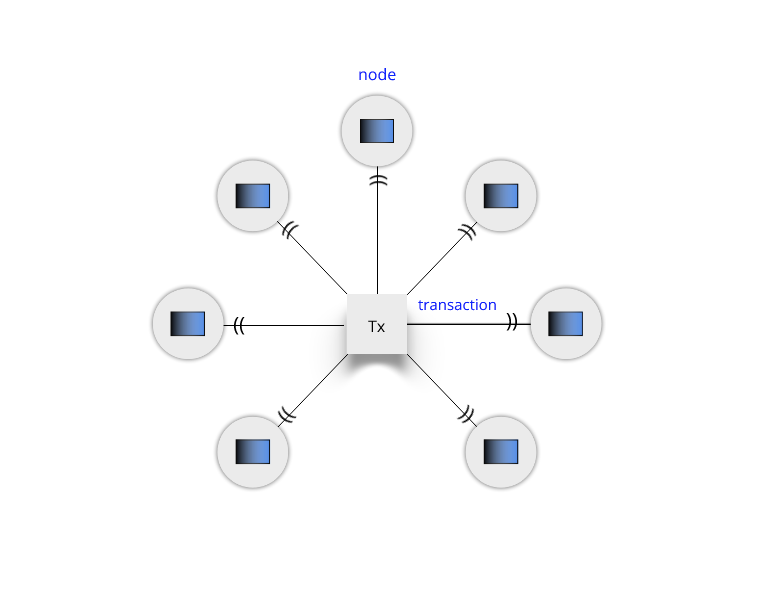
The Mechanism of Transactions and Validation in Blockchain
The blockchain structure is not only about storing data but also about validating and securing transactions. Each transaction within the blockchain architecture represents a digital action, often involving the transfer of value or information. When a transaction is initiated, it is broadcasted to the network, where nodes undertake the crucial task of validation. This process is integral to the architecture of blockchain, as it ensures the legitimacy and integrity of each transaction.
In the structure of blockchain, this validation is typically done through a process known as mining, particularly in public blockchains like Bitcoin. Cryptocurrency mining involves solving complex cryptographic puzzles to validate transactions and add them to a block. Once a transaction is verified and included in a block, it becomes an immutable part of the blockchain structure. This meticulous validation process is what makes blockchain architecture inherently secure and trustworthy.
Ensuring Security and Trust
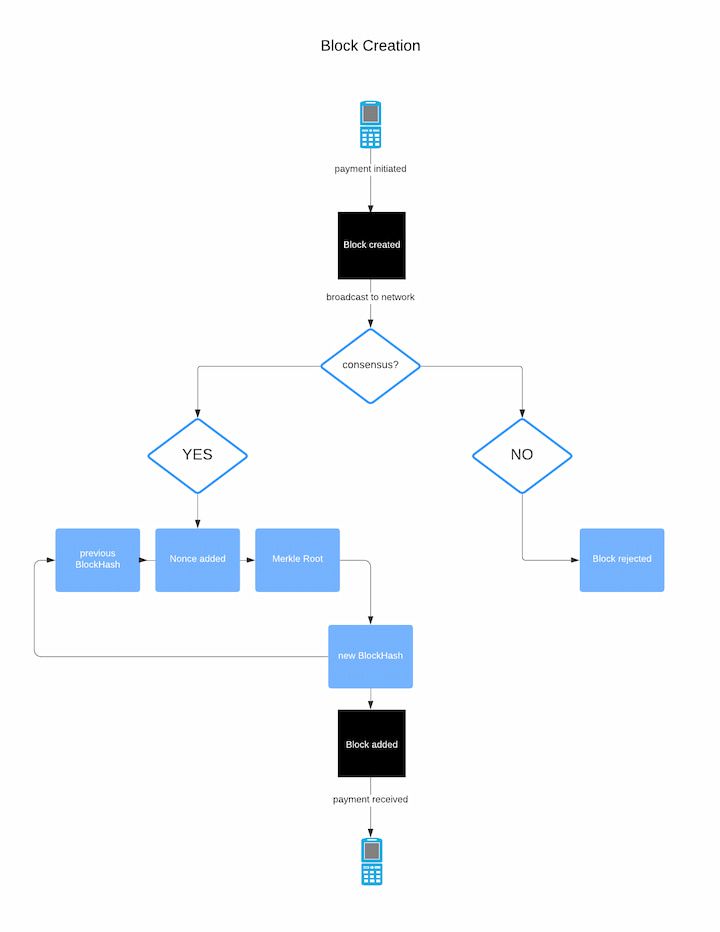
A pivotal aspect of blockchain architecture is the mechanism used to achieve consensus among the various nodes in the network. This consensus mechanism is crucial in the structure of blockchain as it ensures all participants agree on the ledger's current state. In many public blockchains, the proof-of-work system is employed as a part of this consensus process.
This system, integral to the architecture of blockchain, requires nodes (or miners) to solve complex mathematical problems, thus validating transactions and creating new blocks. The proof-of-work model not only secures the blockchain structure but also mitigates the risk of fraudulent transactions and double-spending. It is the backbone of the trust and security that blockchain architecture promises, ensuring that each transaction is accurately recorded and immutable once added to the structure of block in blockchain.
Building a Blockchain Architecture
Developing a blockchain network is a meticulous process that forms the backbone of any blockchain architecture. It involves setting up an infrastructure that adheres to the specific requirements of the intended blockchain structure.
Whether it’s a public, private, or consortium blockchain, each type demands a unique approach to network creation. This network is the foundation upon which the structure of blockchain operates, enabling nodes to interact, transactions to be processed, and consensus mechanisms to be executed.
Key considerations when considering how to build a blockchain include selecting the right consensus algorithm, ensuring scalability, and maintaining security protocols. Tools and platforms, such as Ethereum for public blockchains or Hyperledger for private ones, offer diverse functionalities tailored to different blockchain structures. These tools not only facilitate the creation of a blockchain network but also empower developers to customize the architecture of blockchain to fit specific use cases.
Skill Set for Blockchain Development
To effectively build and maintain a robust blockchain architecture, a diverse skill set is crucial. Developers delving into the world of blockchain structure need a strong foundation in computer science and engineering, coupled with a deep understanding of the specific principles that underpin the architecture of blockchain. Proficiency in blockchain programming languages like Solidity for Ethereum, or Java and Go for Hyperledger, is essential to craft the structure of block in blockchain.
Beyond technical prowess, a successful blockchain developer must also possess an acute awareness of business processes and applications. This dual competency enables developers to not only construct a technically sound blockchain structure but also ensure that it aligns with business objectives and operational requirements. The blend of technical skills and business acumen is key to unlocking the transformative potential of blockchain architecture.
The Transformative Impact of Blockchain Architecture
The implementation of blockchain architecture extends far beyond its origins in cryptocurrency, offering transformative potential across a wide range of industries. The unique characteristics of the blockchain structure—such as decentralization, transparency, and immutability—provide innovative solutions to complex problems in sectors like finance, supply chain management, and healthcare. For instance, in supply chain management, the structure of blockchain enables the creation of transparent and unalterable records of product journeys, from manufacture to sale. In the financial sector, the architecture of blockchain streamlines transactions, reduces fraud, and enhances security. Furthermore, the blockchain structure is instrumental in developing smart contracts that automate and enforce contractual agreements without intermediaries. These diverse applications underscore the versatility and wide-reaching benefits of blockchain architecture, marking it as a key driver of future technological and economic innovation.
Conclusion
As we have explored, the blockchain architecture is not just a technological marvel but a catalyst for innovation across various sectors. Its robust structure of blockchain, characterized by decentralization, security, and transparency, paves the way for a future where digital transactions and record-keeping are revolutionized. From the intricate structure of block in blockchain to the comprehensive architecture of blockchain, this technology offers a plethora of opportunities for businesses, governments, and individuals alike.
As the world continues to digitalize, the significance and applicability of blockchain architecture will only grow, making it an essential area of exploration and investment. For those at the forefront of technology and business, understanding and leveraging the potential of blockchain structure will be key to driving innovation and achieving competitive advantage in the digital era.
FAQ
What are the key elements that make a blockchain secure?
Decentralization: The absence of a central authority reduces the risk of a single point of failure and makes the network more resilient against attacks.
Cryptographic Hashing: Each block contains a unique cryptographic hash of the previous block, making it nearly impossible to alter any block without changing all subsequent blocks.
Consensus Mechanisms: Techniques like Proof of Work (PoW), Proof of Stake (PoS), and others ensure that all nodes agree on the current state of the blockchain, preventing fraudulent transactions and double-spending.
Immutability: Once data is recorded on the blockchain, it cannot be altered or deleted, ensuring a permanent and unalterable record of all transactions.
Transparency: Public blockchains allow anyone to verify and audit transactions, which enhances trust and security by making the network open and verifiable.
Smart Contracts: These self-executing contracts automatically enforce the terms of agreements, reducing the need for intermediaries and minimizing the risk of tampering or disputes.
What differentiates public, private, and hybrid blockchains?
Public Blockchains:
- Access: Open to anyone who wants to join and participate.
- Decentralization: Highly decentralized with numerous participants (nodes).
- Transparency: All transactions are visible to the public.
- Examples: Bitcoin, Ethereum.
Private Blockchains:
- Access: Restricted to specific participants chosen by a central authority.
- Decentralization: Limited decentralization; control lies with a single organization or a group.
- Transparency: Transactions are only visible to permitted participants.
- Examples: Hyperledger, R3 Corda.
Hybrid Blockchains:
- Access: Combines elements of both public and private blockchains, with some data accessible to the public and other data restricted.
- Decentralization: Partially decentralized, balancing transparency and control.
- Transparency: Selective transparency based on the needs of the network.
- Examples: Dragonchain.
How can blockchain architecture transform industries beyond finance?
Supply Chain Management:
- Traceability: Blockchain provides an immutable record of product history, from manufacture to sale, ensuring transparency and authenticity.
- Efficiency: Automates tracking and reduces paperwork, leading to more efficient operations.
Healthcare:
- Patient Records: Securely stores and shares patient records across healthcare providers, improving care coordination and data integrity.
- Drug Traceability: Ensures the authenticity of pharmaceuticals by tracking their journey through the supply chain.
Real Estate:
- Property Transactions: Streamlines the process of buying and selling property by recording ownership and transaction details on the blockchain, reducing fraud and errors.
- Smart Contracts: Automates and enforces real estate agreements, making transactions faster and more reliable.
Voting Systems:
- Security: Ensures that votes are securely recorded and counted, reducing the risk of tampering and fraud.
- Transparency: Provides a transparent and verifiable record of the voting process, enhancing trust in election results.
Intellectual Property:
- Protection: Records ownership and transfer of intellectual property rights, ensuring creators are credited and compensated for their work.
- Royalty Distribution: Automates the distribution of royalties through smart contracts, ensuring timely and accurate payments.
Energy Sector:
- Peer-to-Peer Energy Trading: Enables direct trading of energy between producers and consumers, promoting decentralized energy markets.
- Grid Management: Enhances the management of energy grids by providing real-time data and automated processes.
📧Komodo Newsletter
If you'd like to learn more about blockchain technology and keep up with Komodo's progress, subscribe to our newsletter. Begin your blockchain journey with Komodo today.

